BP03B – Onboarding of a new data space - Participant End-User
To help understand the content of this document, readers should familiarize themselves with the key definitions and actors.
Overview
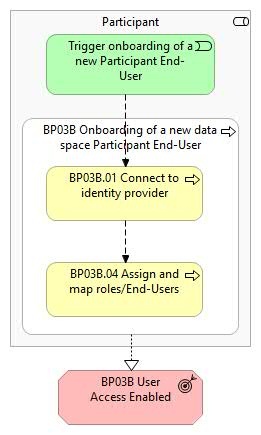
This business process covers the onboarding process for a new Participant End-User. Before Participant End-Users can participate, the Participant must be successfully onboarded into the data space (Business Process 3A).
It includes the following main steps:
- Connect to identity provider: For onboarding the Participant End-User, the Participant must link its local preferred authentication mechanism to the identity provider of the Simpl-Open agent. This allows the Participant to assign their users one ore more roles enabling the access to the Simpl-Open Agent functionality.
- Assign and map roles/End-Users: The Participant assigns data space user roles by mapping them with roles retrieved from the local preferred authentication mechanism. This ensures that each End-User has the appropriate access and permissions within the data space.
Actors
The following actors are involved:
- Participant
Assumptions
The following assumptions are made:
- The Participant already has an existing authentication mechanism and intends to use it to verify access of their End-Users into the Simpl-Open Agent.
- Local preferred authentication mechanism: The Participant must have a local preferred authentication mechanism available to use for verification of the Participant End-User identity.
- Data space list of available roles: The Governance Authority should share a copy of the list of predefined roles that can be used within the data space. The provision of this list is necessary for the Participant to map the internal role directory to the available data space roles of the identity provider that is provided by the Governance Authority.
Prerequisites
The following prerequisites must be fulfilled:
- Data space is configured: The Governance Authority has defined the onboarding procedure and identity attributes relevant for the data space (Business Process 2).
- Participant Onboarded: The Participant should have successfully completed the onboarding business process (Business Process 3A).
Details
The following shows the detailed business process diagram and gives the step descriptions.
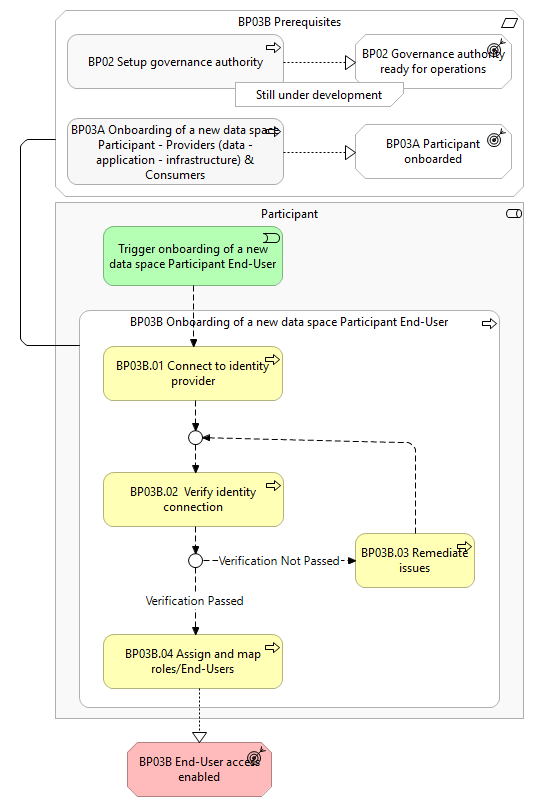
Trigger onboarding of a new data space Participant End-User
The Participant initiates the preparation and submission of the onboarding request.
BP03B.01 Connect to identity provider
The Participant initiates and connects its local preferred authentication mechanism with the identity provider of the Participant Simpl-Agent.
BP03B.02 Verify identity provider connection
The Participant verifies whether the local preferred authentication mechanism has successfully connected with the identity provider. As an outcome of this step:
- If the identity provider connection passed the verification check, then the process moves to step BP03B.04.
- If the identity provider connection fails the verification check, then the process moves to step BP03B.03.
BP03B.03 Remediate issues
The Participant is offered the opportunity to correct issues or deficiencies identified during the verification process. After the corrections are made the applicant can return to step BP03B.02 to retry the identity provider connection.
BP03B.04 Assign and map roles/End-Users
The Participant assigns data space user roles by mapping them with roles retrieved from the local preferred authentication mechanism. This ensures that each End-User has the appropriate access and permissions within the data space.
Outcomes
- User access enabled: The End-User can access the participant's agent and is authorised to perform actions based on their role. This enables the End-User to access the data space and act on behalf of the Participant.
| Business Process | Status: Proposed |
High Level Requirements
3B.1 - Access control - roles management
Simpl shall support the management of ...

Moderator note: Comments are from the previous discussion platform.
Submitted by Luis Carlos BU… on Mon, 25/03/2024 - 14:34
The Description of the high-level requirement should also include provision for the possible withdrawal of participants in Dataspaces. Also, the middleware will provide the tools for easy identification of dead users and participants.
Submitted by Mark Dietrich on Thu, 04/07/2024 - 14:16
Luis mentions withdrawal. There must also be procedures for "sanction" and possible "removal" of non-compliant participants from a Data Space.
In reply to Luis mentions withdrawal. … by Mark Dietrich
Submitted by Rick Santbergen on Thu, 25/07/2024 - 10:28
Hi Mark, at the moment there is no “sanction” procedure foreseen to be implemented as software functionality and in any case every Dataspace Governance Authority will manage it outside Simpl-Open
Submitted by Andreas Eisenrauch on Fri, 16/08/2024 - 11:02
I am not sure, if the human end users are really relevant for the data space governance authority. I have doubt, that they will acquire connectors for getting an airlines flight schedule or a museum catalogue directly from the source. Instead, they will register to applications (developed in use case projects) provided by corporate participants, which retrieve the data from partners in the DS. I think this, item has no high priority at least.
Please log in or sign up to comment.